Announcement: Upcoming changes to the permission grant flow for OAuth apps

This announcement is intended for app developers who use the Zoho API console.
We're going to implement an important update to the way users grant permission for the OAuth apps created through the API console.
What’s changing?
Currently, users can grant access to your app even if they do not have an account in any of the Zoho apps included in the requested OAuth scopes. Starting February 10, 2025, this will no longer be allowed when certain apps are included in the request. These apps include the below:
|
- Bigin
|
- PhoneBridge
|
|
- Campaigns
|
- QEngine
|
|
- CRM
|
- Recruit
|
|
- Desk
|
- Solution
|
|
- IOT
|
- ZeptoMail
|
|
- Marketing Automation
|
|
From the effective date, when scopes of any of the above apps are included in a request:
- Users must have an account in the specified Zoho apps requested by your OAuth app to grant access to the required permissions.
- If a user doesn't have an account in even one of the Zoho apps mentioned, they will be unable to grant permission.
- The "Accept/Reject" buttons will be replaced with the "Back to app" button. When users click this, "error=no_org" will be sent as response to your app's redirect URL.
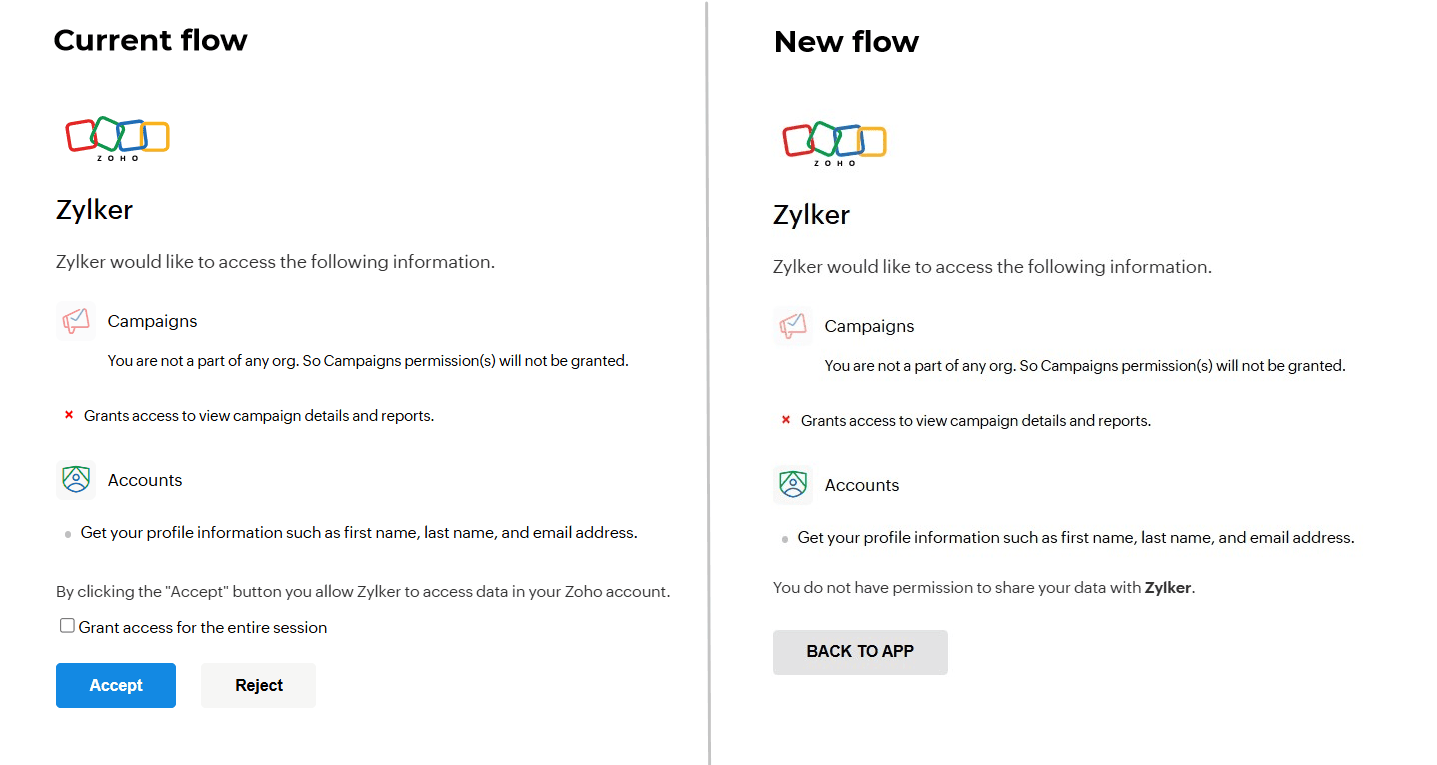
Why this change?
This change is to make sure the users don't encounter any issues with the apps they've granted access to. If there is no resource to access, the app will not work properly even if the user has granted the necessary permission. This results in poor user-experience.
Also, when an OAuth app requests specific permissions, it indicates those scopes are essential for the app to function. If any scope is not relevant for the app, those permissions shouldn't be requested to the user.
Recommended actions for app developers
The existing refresh tokens generated for such cases will continue to work. But if the user revokes the permission, they won't be able to grant access to the app again (if they still don't have accounts in the required Zoho apps).
Hence, make sure to audit your apps to ensure they only request scopes that are essential. And, update your app to handle the scenario where authorization fails due to users not having required accounts.
If you have any questions or need support regarding this change, please reach out to us at support@zohoaccounts.com.
Topic Participants
Abdul Aleem
Sticky Posts
Deprecation of SMS-based multi-factor authentication (MFA) mode
Overview of SMS-based OTP MFA mode The SMS-based OTP MFA method involves the delivery of a one-time password to a user's mobile phone via SMS. The user receives the OTP on their mobile phone and enters it to sign into their account. SMS-based OTPs offer
Recent Topics
User marked as SPAMMER. Mail Fetch has also been disabled for any active POP accounts.
I am the administrator for joelles.com One of our accounts has been blocked saying this: User marked as SPAMMER. Mail Fetch has also been disabled for any active POP accounts. I cannot change the disabled account in the control panel as it says that itMy domain did not activate
Hi, my domain (apsaindustrial.com.ar) did not activate, and the phone verification message never arrived. Please would you solve this problem? Thanks.ME SALE ESTE ERROR: No fue posible enviar el mensaje;Motivo:554 5.1.8 Email Outgoing Blocked
Ayuda!! Me sale este error al intentar enviar mensajes desde mi correo electronico de Zoho! Tampoco recibo correos pues cuando me envia rebotan. Ayuda, Me urge enviar unos correo importantes!! Quedo atenta MAGDA HERNANDEZ +5731120888408Is there a way to sync Tags between CRM and Campaigns/Marketing Hub?
I wonder if there is a way to synch the tags between CRM and Marketing-Hub / Campaigns?how to see if a specific contact opened an email in zoho campaign?
how to see if a specific contact opened an email in zoho campaign?Revenue Management: #8 Revenue Recognition in Educational & Training Institutions
Educational Institutions and training centres typically collect course fees at the time of enrolment, sometimes for a one-day workshop and sometimes for a year-long certification course. You might also charge separately for course materials or evaluation.How to Customize Task Creation to Send a Custom Alert Using JavaScript in Zoho CRM?
Hello Zoho CRM Community, I’m looking to customize Zoho CRM to send a custom alert whenever a task is created. I understand that Zoho CRM supports client scripts using JavaScript, and I would like to leverage this feature to implement the alert functionality.Using files from Zoho CRM in Gemini/ChatGPT/Claude
Hi all, I’ve got subscriptions to Gemini and a few other AI tools which I use for tasks like data enrichment, email composition, etc. In our workflow, we often receive various documents from clients — such as process workflows, BRDs/requirement documentsEnhancements to the formula field in Zoho CRM: Auto-refresh formulas with the "Now" function, stop formula executions based on criteria, and include formulas within formulas
Dear Customers, We hope you're well! By their nature, modern businesses rely every day on computations, whether it's to calculate the price of a product, assess ROI, evaluate the lifetime value of a customer, or even determine the age of a record. WithMaximum file limit in zoho people LMS
Dear Team, I am having approximately 4.9 GB of material, including PPTs and videos for uploading in zoho people LMS course. May I know what is the maximum limit limit for the course files Thanking you, With regards, Logeswar V Executive _ OperationsDynamically prefill ticket fields
Hello, I am using Zoho Desk to collect tickets of our clients about orders they placed on our website. I would like to be able to prefill two tickets fields dynamically, in this case a readonly field for the order id, and a hidden field for the sellerOptimize your Knowledge Base for better visibility by allowing search engine crawling and indexing
All you need to know about no-follow and no-index in KB. What are article crawlability and indexability? Crawlability and indexability are vital for making an article visible and accessible to search engines. When a search engine crawls an article, itHas anyone created a public ASAP Guide that I can check out?
I am thinking of adding an ASAP guide to my web application, but I have noticed that the ASAP widget itself can be really slow to load sometimes. Has anyone created a public ASAP Guide that I can check to see how performant it is? I don't want to spendZoho Desk Partners with Microsoft's M365 Copilot for seamless customer service experiences
Hello Zoho Desk users, We are happy to announce that Zoho Desk has partnered with Microsoft's M365 to empower customer service teams with enhanced capabilities and seamless experiences for agents. Microsoft announced their partnership during their keynoteWhat’s New in Zoho Analytics – September 2025
Hello Users!! In this month’s update, we’re raising the bar across multiple touchpoints, from how you bring in data, plan and track projects to how you design and brand your dashboards. We’ve added the all-new Gantt chart for project visualization, expandedZoho MCP has no tools for Creator or 3rd Party Apps?
I don't see a Zoho MCP community forum so putting this here. Two big problems I see: 1) Although Zoho advertises "over 950 3rd party apps" as available through their MCP, when I go to "Add Tools" there are ZERO 3rd party apps available to choose from.Zoho Forms - Zoho Drive connection - Shared Drives not supported
Hello i am stuck with Google Drive Connection There is no supported shared drives Connection is not support shared drives boolean Query Parameters - supportsAllDrives=true&supportsTeamDrives=true to activate fetch files from the shared drives. Ahat needCan't create package until Bill created?
I can't understand why we cannot create a package until a Bill is created? We are having to created draft Bills to create a package when the item is received, but we may not have received a Bill from the supplier. Also, Bill # is required, but we normallyWhats the Time out Limit for API Calls from Deluge?
Hi Creator Devs, We are making API calls to third party server via Deluge. Getting this error message: Error at line : 24, The task has been terminated since the API call is taking too long to respond. Please try again after sometime. Whats the defaultHow to get the authorization code for domain transfer from Zoho?
I have transferred my domain from zoho to godaddy, and that needs a authorization code. I haven't got any mail containing that. How to get the authorization code from domain transfer? Thanks, ArunI have error AS101 when I try to add paypal@mydomain.com to Zoho
Please help me with this. I tried to call the help line 4 times but don't get any response.Tip #3: How to change your booking page language
Displaying your booking page in your target audience's language can greatly increase customer satisfaction. By speaking their language, you will help customers feel more comfortable scheduling with you and create a stronger connection with them. Let'sHow can I optimize a Zoho Site page for SEO when embedding external menu or restaurant links?
Hi everyone, I’m experimenting with building small content hubs on Zoho Sites and want to make sure I’m doing it in an SEO-friendly way. For example, I tried creating a page that highlights restaurant menu items and linked out to a resource like this:Diff signature for compose new email and replies
Hi, How do i have different signature for replies and new emails. its inconvenient to have one large signature for replies. Usually on Outlook we have the option to keep separate signatures for new emails and for replies.Zoho Website Site Speed Up & Setting
We are experiencing slow loading speeds on our Zoho website and would like assistance in optimizing its performance. Kindly review the site and suggest or implement necessary improvements to enhance speed, especially related to: > Caching mechanisms >Clickjacking: Zoho Vault's Response
Issue: Password manager browser extensions are found to be vulnerable to clickjacking security vulnerabilities that could allow attackers to steal account credentials, TFA codes, and card details under certain conditions. Reported by: Marek Toth, IndependentRefund
Hi There, Please refund me asap possible, because of no support given. Thank youNo option for pick up in Zoho Books / Inventory but yes on commerce
Is it planned to release soon on books/inventory?Accessing Zoho form enteries via API
Hi As a user I can view enteries to a form at: https://forms.zoho.com/<myOrganisation>/report/<myReportName>/records/web How do I access these entries via API? I don't have any problem with scope and getting tokens. But I have no idea what the API callBlueprint Issue - Being able to set a subform field as mandatory
I'm creating a blueprint. My record involves a subform which is only shown once field is set but the field gets set in step two of the process. My problem - I can't save the record as the subform field is set to mandatory - If I unset the mandatory field,Blueprint - Mandatory file upload field
Hi, File upload (as we as image upload) field cannot be set as mandatory during a blueprint transition. Is there a workaround? Setting attachments as mandatory doesn't solve this need as we have no control over which attachments are added, nor can weZoho Books - Include Quote Status in Workflow Field Triggers
Hi Zoho Books team, I recently tried to create a Workflow rule based on when a Quote is Accepted by the customer. This is something which I thought would be very easy to do, however I discovered that Status is not listed as a field which can be monitoredZoho Books - Show Related Sales Orders on Quotes
Hi Books team, I've noticed that the Quotes don't show show the related Sales Order. My feature request is to also show related Sales Orders above the Quote so it's easy to follow the thread of records in the sales and fulfilment process. Below screenshotAdd VAT/Tax line to bank adjustments
When categorising transactions and matching bank feeds with transactions such as customer payments, we use the "Add Adjustment" to add things like fees/bank fees. It would be useful to choose a VAT/Tax rate here. Whilst there is a bank charges option when adding a payment, this goes into the default bank charges account. We use the adjustments so that we can choose the account and separate our fees. We use different card providers and Worldpay charges VAT so we are stuck. We cannot integrate withNew Menu Layout Feedback
I'd really like to see the banking item back on the top of the menu. I'm sure part of it is just because that's what I'm accustomed to. However, for a bookkeeping program, I think there's a logic to having banking be on top. Not a giant issue, but somethingHow to use Rollup Summary in a Formula Field?
I created a Rollup Summary (Decimal) field in my module, and it shows values correctly. When I try to reference it in a Formula Field (e.g. ${Deals.Partners_Requested} - ${Deals.Partners_Paid}), I get the error that the field can’t be found. Is it possibleForm Accessibility
Hi, is there an update on the accessibility standard of Zoho forms? Are the forms WCAG 2.1 AA compliant?Cannot schedule report delivery
The only 'send option' available when exporting reports is 'immediately' The option to schedule the report is missing.adding attachment in sendmail script where attachment is in a CRM field
Hi all, I have a custom field of type 'File Upload' in one of my modules in my CRM. I want to include the file in that field as an attachment to an email - which is done from a button on the 'Results' module. I have created a script and a button to initiate an email from that module. The Deluge scripting window has allowed me to add arguments for all the fields I need to use except for the one file upload type field. My script currently looks like the below (content of the email omitted). As you[Free Webinar] Learning Table Series - AI-Enhanced Insurance Claim Management in Zoho Creator
Hello Everyone! We’re excited to invite you to another edition of Learning Table Series, where we showcase how Zoho Creator empowers industries with innovative and automated solutions. Struggling with lengthy claim processes, a lack of visibility intoNext Page