Tip #23- Enhancing security during remote support sessions- 'Insider Insights'
Hello Zoho Assist Community!
We are back again this week with another setting from Preferences: Security. Ensuring the security of remote support sessions is crucial, especially when sensitive data is frequently accessed during these interactions. It’s important to implement robust security measures to protect both the technician and the customer. In this post, we will discuss essential security settings that can significantly enhance the safety of your remote support sessions.
Disabling clipboard sharing
Clipboard sharing can be a potential security risk as it allows the technician or customer to copy and paste information between computers. Imagine you are providing support to a client handling confidential financial data. By disabling clipboard sharing, you ensure that sensitive information cannot be inadvertently or maliciously transferred to or from the client's system. To implement this:
Click the checkbox next to Disable Clipboard Sharing.
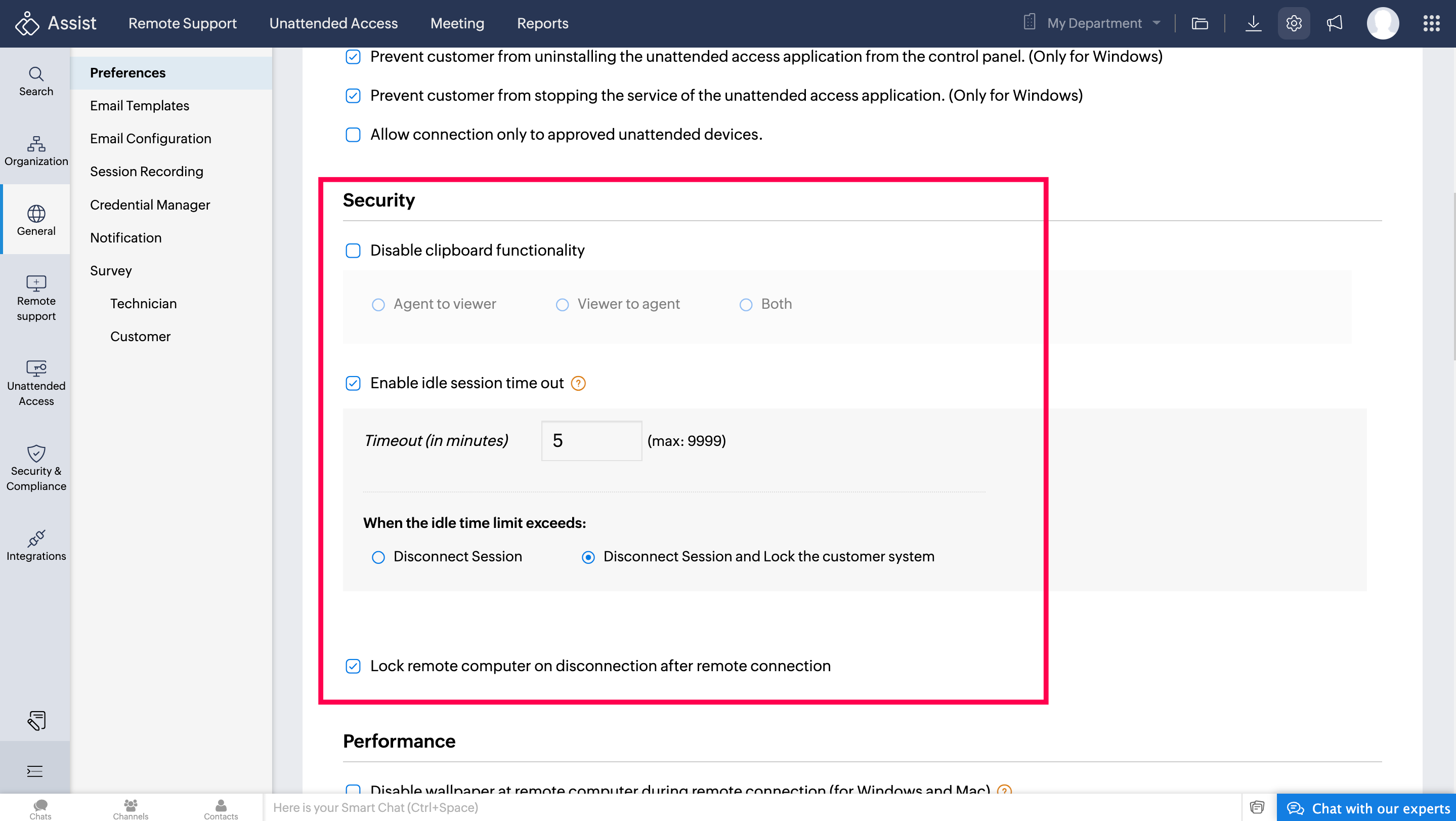
Enabling idle session timeout
Picture a situation where a technician is remotely working on a client’s server to perform routine maintenance. Another client steps in with an urgent requirement, and the technician gets caught up with the other device, leaving the session unattended. Enabling the idle session timeout ensures that if the session remains inactive for too long, it will automatically end, protecting the server from any unauthorized access during the client's absence.
An idle session can be a significant security vulnerability. You can enable an idle session timeout to automatically terminate a session if the technician's computer is left idle for a specified duration. A reminder will pop up 90 seconds before the session ends, giving the technician the option to continue or end the session. To enable this:
Click the checkbox next to Enable Idle Session Timeout.
Fill in the desired timeout period in minutes in the space provided. Choose Disconnect session to terminate the session or Disconnect session and lock the remote computer to lock the remote computer also.
Locking the remote computer post-session
To add an extra layer of security, you can configure the remote computer to lock automatically at the end of every support session. After finishing a remote troubleshooting session, locking the remote computer ensures that no one can access it until a legitimate user logs back in, maintaining the security of the client's system. By configuring these settings, you can provide secure and efficient remote support, ensuring that your client's data remains protected.To enable this:
Click the checkbox labeled Lock remote computer on disconnection after remote connection.
All-in-one knowledge management and training platform for your employees and customers.
Zoho Developer Community
Topic Participants
Amali Steffi Raj J
Zoho TeamInbox Resources
Zoho CRM Plus Resources
Zoho Books Resources
Zoho Subscriptions Resources
Zoho Projects Resources
Zoho Sprints Resources
Qntrl Resources
Zoho Creator Resources
Zoho CRM Resources
Zoho Show Resources
Get Started. Write Away!
Writer is a powerful online word processor, designed for collaborative work.
-
オンラインヘルプ
-
Webセミナー
-
機能活用動画
-
よくある質問
-
Ebook
-
-
Zoho Campaigns
- Zoho サービスのWebセミナー
その他のサービス コンテンツ
Nederlandse Hulpbronnen
ご検討中の方
Recent Topics
Client Portal ZOHO ONE
Dear Zoho one is fantastic option for companies but it seems to me that it is still an aggregation of aps let me explain I have zoho books with client portal so client access their invoice then I have zoho project with client portal so they can access their project but not their invoice without another URL another LOGIN Are you planning in creating a beautiful UI portal for client so we can control access to client in one location to multiple aps at least unify project and invoice aps that wouldSearch not working!
I have items in my notebook tagged but when I search for a tag nothing comes up! Any fix for this?ERROR CODE :550 - 550 5.1.1 Invalid email recipients
This message was created automatically by mail delivery software. A message that you sent could not be delivered to one or more of its recipients. This is a permanent error. mustafa.ashraf@techlink-eg.net, ERROR CODE :550 - 550 5.1.1 Invalid email recipientsWhat's New in Zoho POS - February 2026
Hello everyone, Welcome to Zoho POS’s monthly updates, where we share our latest feature updates, enhancements, events, and more. Let’s take a look at how February went. Purchase and sell items on different units We have introduced a unit conversion functionalityCan i integrate bigin with google voice?
I make all my calling through google voice to seprate my personal line from business. I want to log my calls with customers automatically but i domt see anywhere where i can do that. Any help? Im pretty sure i wont be able to. SadPOP/SMTP access authentication failed
I am unable to log setup outlook for my zoho mail account. I am using these settings poppro.zoho.com port 995 SSL smtp.zoho.com port 587(tls)/465(ssl) username/password works on mail.zoho.com but not with POP access. Can you help?Depositing funds to account
Hello, I have been using Quickbooks for many years but am considering moving to Zoho Books so I am currently running through various workflows and am working on the Invoicing aspect. In QB, the process is to create an invoice, receive payment and thenOur Review Of Zoho CRM after 60 Days
The purpose of this is to just share with Zoho why I love their product, but ultimately why I could not choose Zoho CRM for our next CRM. About two months ago we begun a CRM exploration process for our financial planning firm, based in Texas. We alreadyError AS101 when adding new email alias
Hi, I am trying to add apple@(mydomain).com The error AS101 is shown while I try to add the alias.Enhancement in Zoho CRM: Control who gets to participate in a forecast by customizing the user hierarchy
Include only users from the sales function; exclude the rest Dear Customers, We hope you're well! We started this year with a series of exciting enhancements to Zoho CRM and to this list, we are thrilled to add an enhancement to forecasting. Let's talkThis domain is not allowed to add. Please contact support-as@zohocorp.com for further details
I am trying to setup the free version of Zoho Mail. When I tried to add my domain, theselfreunion.com I got the error message that is the subject of this Topic. I've read your other community forum topics, and this is NOT a free domain. So what is thePossible to generate/download Quote PDF using REST API?
See title. Is there any way after a quote has been created to export to a PDF using a specified template and then download it? Seems like something that should be doable. Is this not supported in the API v2.0?Allow Admin to Configure Report > More Options Button
As an Admin, I want to configure the options of the Report > More Options button to improve UX and reduce Developer overhead. See attached screenshot. Original question posted here: https://help.zoho.com/portal/en/community/topic/modify-standard-repGenerate a link for Zoho Sign we can copy and use in a separate email
Please consider adding functionality that would all a user to copy a reminder link so that we can include it in a personalized email instead of sending a Zoho reminder. Or, allow us to customize the reminder email. Use Case: We have clients we need toMultiple Zoho One accounts
Hello. I'm searching for a solution to run multiple organizations under 1 Zoho One account or have a different Zoho One account for each organization and still be able to easily login to each. Currently Zoho One doesn't allow the same email address toManage Every Customer Conversation from Every Channel inside Zoho SalesIQ
Your customers message you from everywhere. But are you really able to track, manage, and follow through on every conversation, without missing anything? With interactions coming in from websites, mobile apps, and messaging platforms like WhatsApp andYou cannot send this campaign as there is no contact in the selected mailing list.
We have synced contact lists and sent campaigns just fine prior to today. Now no matter what list I upload when I go to send the campaign it gives an error "You cannot send this campaign as there is no contact in the selected mailing list." And now itCustom view inconsistencies
Why is "is not" missing from criteria, along with other comparison operators ??? It makes it almost impossible to build required custom views, I don't want "void" invoices listed & why on earth would "Void" invoices be showing when the criteria includesPivot Report Formula - using a today() variable
Is it possible for me to use a value of today() in a formula on a pivot table? I'm trying to identify where the end date of a project is greater than the current date if("10. Projects (Zoho Projects).End Date" > today(), 'Yes', 'No') I get the error thatCannot connect IMAP to outlook
Hello I have followed the instructions to connect my zoho account to Outlook IMAP but get this message: Session Id: bba118fb-151c-824f-9512-3ad1e91b109d Timestamp: 1708976566964 Error code: INVALIDCREDENTIALS INTERACTIONREQUIRED I'm using the exact configerationDepartment Overview by Modified Time
We are trying to create visuals to show the work our agents do in Zoho Desk. Using Zoho Analytics how can we create a Department Overview per modified time and not ticket created time? In order for us to get an accurate view of the work our agents areWhere is the settings option in zoho writer?
hi, my zoho writer on windows has menu fonts too large. where do i find the settings to change this option? my screen resolution is correct and other apps/softwares in windows have no issues. regardsEnhance Sign CRM integration
Hello all, I'm working on a custom Deluge script to enhance the integration between Zoho CRM and Sign by using a writer merge template for additional flexibility. I want to replicate the post-sign document integration that exists between CRM and SignZoho Workdrive download was block by security software
Hi Team, Recently workdrive download was blocked by huorong security. Could you please advise how to put zoho workdrive as white list? every time we put "*.zohoexternal.com" or "workdrive.zohoexternal.com", the warning msg will still pop in next dowChoosing a portal option and the "Unified customer portal"?
I am trialling Zoho to replace various existing systems, one of which is a customer portal. Our portal allows clients to add and edit bookings, complete forms, manage their subscriptions and edit some CRM info. I am trying to understand how I might bestGeneral feedback
I think Zoho is at the moment (potentially) the best, or perhaps the only, real online solution, for business, and not just business. Surely the only one that has all the features that I need (and I've probably tried everything, at least all that has a cost-free option). It has still got lots of bugs and imperfect features, so I do hope it keeps developing and becomes a really professional platform. Lots of people (including me) want to use such one platform for all scheduling/mail/note-taking...How to add SSL to Short URL custom domain?
Hi, I've added a custom domain the the URL Shortener Domains. It's creating the short URL fine, but when clicking through, firstly I get an SSL warning, then a 400 Bad Request warning.Single Portal for Multiple Apps
Hello, I'm just getting started with Zoho and I'm very overwhelmed. I am currently using the free trial of Zoho One, but if I can figure it out, I intend to upgrade to the paid version. Zoho One, of course, gives me access to an entire suite of services/applications. One of the things I'd like to do is have a single place for clients (customers?) to log in and view current projects, invoices, contact information, etc. A single login for my clients. A single portal. I've come across documentationAntispam validation failed for your domain in Accounts
I tried adding a domain to zeptomail.zoho.com, but the “add domain” operation failed. The front‑end error reads: “Domain could not be added. Please contact support@zeptomail.com.” The back‑end API returned: ``` { "error": { "code": "TM_3601", "details":Define your custom business logic in Zoho Projects
Every organization has a defined way of executing projects. There are clear expectations around how tasks should move, when projects should progress, and which actions require validation. When these rules are consistently followed, projects remain structuredCancelled appointments still block out timeslot
I haven't had to test this before, but I've just found a problem. I had an appointment in a certain timeslot, and that appointment was cancelled. However, Bookings won't let another appointment be booked in that slot - it makes that time unavailable untilPreventing Group Emails From Being Sent to Group Member Personal Mail
We have a group setup for a public facing email address. We have streams turned on for this group. Right now when an email is sent to this group email it hits the group stream and also sends a copy of the email to all group members. We'd like to disableUnusual activity detected from this IP. Please try again after some time.
Hello Zoho admin and IT team We are a registered website in Eloctronic services and we been trying to add our users to the zoho system but this issue faced us ,, hope you unlocked us please.On Edit Validation Blueprint
Hello, I have a notes field and a signature field. When the Approve button is clicked, the Signature field will appear and must be filled in. When the Reject button is clicked, the Notes field will appear and must be filled in. Question: Blueprint will¿Puedo migrar mi sitio desde WordPress a Zoho? ¿Zoho admite herramientas con código personalizado?
¡Hola comunidad! Estoy evaluando la posibilidad de migrar mi sitio web https://calculadoradenotas.cl/ desde WordPress a una solución Zoho, y tengo algunas dudas técnicas que espero puedan aclararme. Mi sitio no es solo informativo: es una herramientaHow do I link my invoice to an estimate?
There has been instances where I have created estimates, however, invoices for the same estimate were created independently. The status of these estimates hasn't converted to 'invoiced'.Zoho Books (and other finance suite apps) - Retrospective Linking of Invoice and Sales Orders to Quotes.
In some cases, Quotes and Invoies may be created sperately instead of using the convert feature. In this feature request I am asking for the Finance Suite team to consider adding a lookup field to reference the quote on Invoices and Sales Orders, or someImpossible to import Journal from Freshbooks
I have been trying to import journals from Freshbooks since August 30th. Every time I try to import, I get an error message. I have already made sure every row has a date. First it was saying the account and notes had unexpected input and that every debit/creditZoho Payroll's USA and KSA editions are available in Zoho One!
Greetings! We’re excited to share that Zoho Payroll, currently available only in India and the UAE, is now introducing the KSA (Kingdom of Saudi Arabia) edition and the USA (United States of America) edition, and these editions are now available in ZohoPeppol: Accept Bill (Belgium)
Hi, This topic might help you if you're facing the same in Belgium. We are facing an issue while accepting a supplier bill received by Peppol in Zoho Books. There is a popup with an error message: This bill acceptance could not be completed, so it wasNext Page












